Configure SSL/TLS inspection and decryption
You can configure SSL/TLS inspection and HTTPS decryption in DPI and web proxy modes.
After decrypting secure web content, Sophos Firewall encrypts the content again using certificates signed by this CA. To prevent untrusted certificate errors, you must install the signing CA on users' endpoints.
Do as follows:
- Check if you have the default SNAT rule to masquerade traffic.
- Configure a web policy.
- Configure a firewall rule for web filtering.
- Apply the inspection and decryption rules and settings.
- Download the signing CA.
- Install it on users' endpoints.
Check the SNAT rule
- Go to Rules and policies > NAT rules.
-
Check the rule list for Default SNAT IPv4.
This is a default SNAT rule to masquerade outgoing IPv4 traffic.
-
If you don't have the rule or want to create a rule for IPv6 traffic, do as follows:
- Click IPv4 or IPv6 above the NAT rule list.
- Click Add NAT rule and click New NAT rule.
- Enter a name.
- Set Translated source (SNAT) to MASQ.
- Click Save.
Add a web policy
This example shows how to add a web policy rule using web categories:
- Go to Web > Policies and click Add.
- Enter a name.
- Click Add rule.
- Under Users, click the drop-down list, clear Anybody, and click Add new item.
- Select the users and groups you want and click Apply selected items.
- Under Activities, click the drop-down list, clear All web traffic, and click Add new item.
- Select Web category in the activity list, select the category you want and click Apply selected items.
- Under Action, select Allow HTTP.
- Click the drop-down list next to the HTTP actions and select Allow HTTPS.
- Under Constraints, select a time to apply the rule.
- Turn Status on.
- Click Save.
Configure a firewall rule
You must configure the web filtering settings in a firewall rule.
- Go to Rules and policies > Firewall rules.
- Click Add firewall rule and then New firewall rule.
- Enter a name.
- Make sure Action is set to Accept.
- Set the Source zones to LAN and Wi-Fi.
- For Source networks and devices, select the local subnets you want.
- Set the Destination zones to WAN.
- Set Destination networks to Any.
- Make sure Services is set to Any.
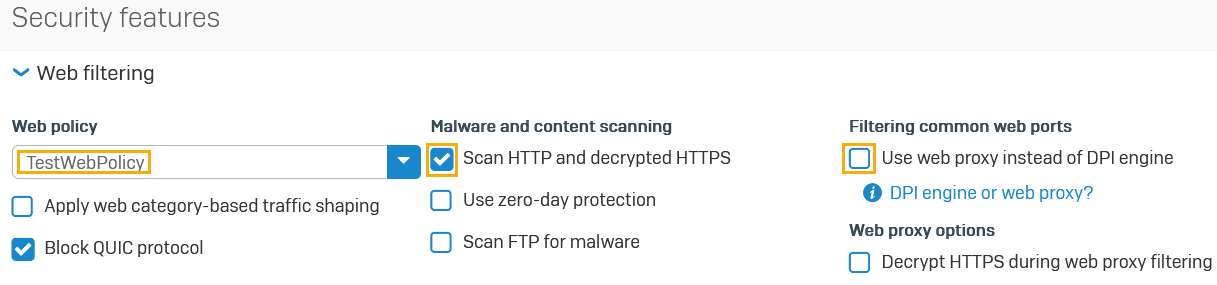
- Under Security features, click Web filtering.
- Select the Web policy you created from the drop-down list.
- Under Malware and content scanning, select Scan HTTP and decrypted HTTPS.
-
Under Filtering common web ports, make sure the checkbox for Use web proxy instead of DPI engine isn't selected.
Here's an example:
-
Click Save.
- Go to Rules and policies > Firewall rules.
- Click Add firewall rule and then New firewall rule.
- Enter a name.
- Change the Action if you want.
- Set the Source zones to LAN and Wi-Fi.
- For Source networks and devices, select the local subnets you want.
- Set the Destination zones to WAN.
- Set Destination networks to Any.
-
Set Services to Any.
If you want to select specific services, choose the options based on your network configuration:
- Transparent proxy: HTTP and HTTPS.
- Direct proxy: HTTP, HTTPS, and the Web proxy listening port you configured under Web > General settings > Web proxy configuration.
-
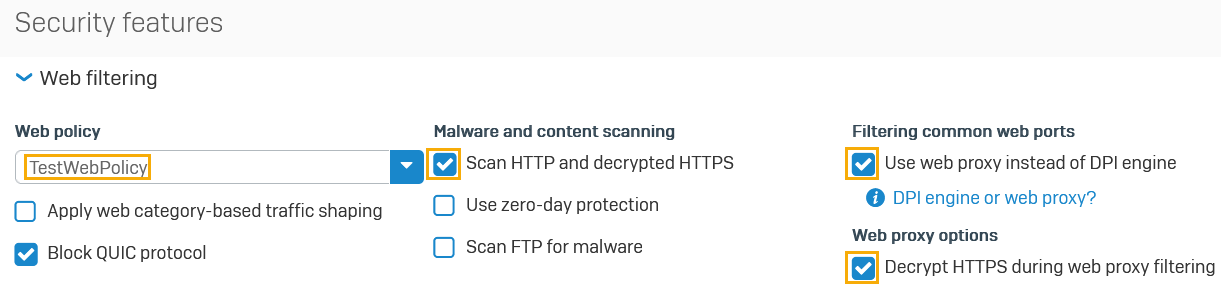
Under Security features, click Web filtering.
- Select the Web policy you created from the drop-down list.
- Under Malware and content scanning, select Scan HTTP and decrypted HTTPS.
- Under Filtering common web ports, select Use web proxy instead of DPI engine.
-
Select Decrypt HTTPS during web proxy filtering.
Here's an example:
-
Click Save.
Apply HTTPS decryption
After inspecting and decrypting secure web content, Sophos Firewall encrypts the content again using certificates signed by the CA you configure. This example shows how to apply the built-in signing CA. To use custom CAs, see Add subordinate and root CAs for TLS traffic.
In DPI mode, you configure SSL/TLS inspection rules.
- Go to Rules and policies > SSL/TLS inspection and click Add.
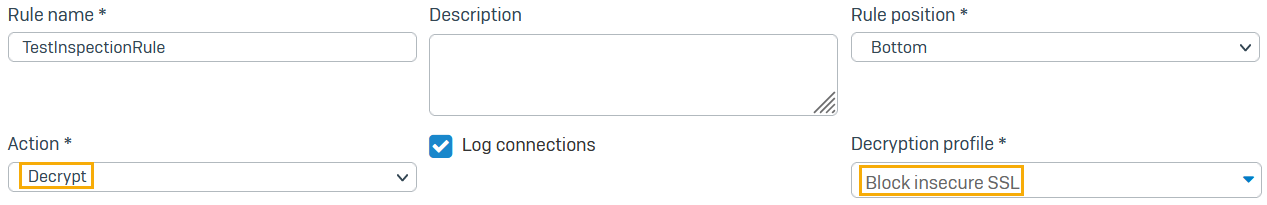
- Enter a rule name.
- Set Action to Decrypt.
-
Set Decryption profile to Block insecure SSL.
You can see its settings in Profiles > Decryption profiles.
-
Set the Source zones to LAN and Wi-Fi.
- For Source networks and devices, select the local subnets you want.
- Set the Destination zones to WAN.
- Set Destination networks to Any.
- Set Services to Any.
- Click Save.
- Go to Web > General settings.
- Scroll down to HTTPS decryption and scanning.
-
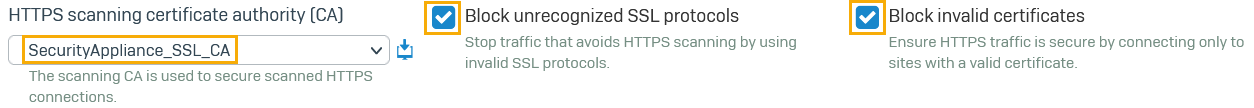
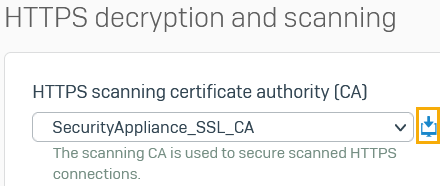
Under HTTPS scanning certificate authority (CA), select a CA to secure scanned HTTPS connections.
You can select the built-in or internal certificate available on Sophos Firewall or use an external CA.
-
Select Block unrecognized SSL protocols.
- Make sure Block invalid certificates is selected.
-
Click Apply.
Here's an example:
-
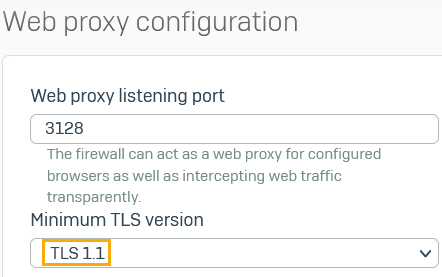
Under Web proxy configuration, make sure TLS 1.1 is selected.
-
Click Apply.
Download the signing CA
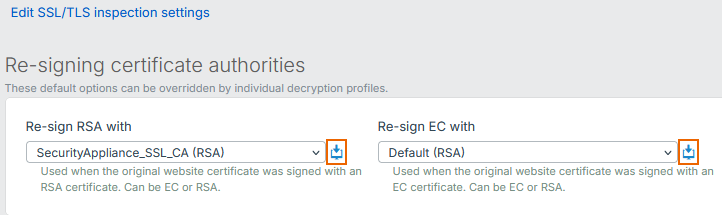
- Go to Rules and policies > SSL/TLS inspection rules and click SSL /TLS inspection settings.
- Under Re-sign RSA with, click the download button
 next to the CA that is selected.
next to the CA that is selected. -
Optional: Under Re-sign EC with, click the download button
 next to the CA that is selected. This is only required if a different CA is selected.
next to the CA that is selected. This is only required if a different CA is selected. -
Click Cancel.
You must do as follows for transparent and direct proxy modes:
- Go to Web > General settings.
- Scroll down to HTTPS decryption and scanning.
-
Under HTTPS scanning certificate authority (CA), click the download button next to the CA you selected.
To prevent untrusted certificate error messages, you must install this CA on your users' endpoints. See Add a CA manually to endpoints.
For direct proxy mode, you must allow the web proxy service for your users' zones. Do as follows:
- Go to Administration > Device access.
- Under Other services > Web proxy, select LAN and Wi-Fi.
- Click Apply.
To install the CA on users' endpoints, see Add a CA manually to endpoints.