General settings
The firewall scans HTTP(S) and FTP traffic for threats as specified by your firewall rules and for inappropriate web usage when a web policy is selected for a rule. These settings apply only to traffic that matches firewall rules with these options set. You can specify the type of scanning, maximum file size to be scanned, and additional checking. You can also create policy overrides to allow end users to access otherwise blocked websites.
Malware and content scanning
Configure general restrictions for scanning and restricting traffic by type and protocol. To turn on malware and content scanning, select Scan HTTP and decrypted HTTPS in the firewall rule.
To decrypt HTTPS and scan it for malware, you must select specific settings based on your configuration.
-
Web proxy mode: You must select Use web proxy instead of DPI engine and Decrypt HTTPS during web proxy filtering in the firewall rule.
-
DPI engine mode: You must set Action to Decrypt in Rules and policies > SSL/TLS inspection rules.
Scan engine selection: Scanning engine to use on all traffic.
-
Single engine: Scans traffic using the primary antivirus engine (by default, Sophos). This selection provides optimal performance.
-
Dual engine: Scans traffic using both engines, first by the primary and then by the secondary. This selection provides maximum recognition rate and security, but may affect performance.
Note
If you're using Zero-day protection, set the single-scan engine to Sophos or select dual-engine scanning.
Web proxy scanning mode: Scanning mode for HTTP and HTTPS traffic. This option only applies to web proxy filtering. The DPI engine always uses real-time mode.
-
Batch: In batch mode, the firewall downloads the file in full and scans it. Only the web proxy can use batch mode. Batch mode offers maximum protection, but it may affect browsing performance because it uses the full bandwidth. Traffic shaping is applied when the file is passed to the browser.
-
Real-time: In real-time mode, the downloaded file content is passed to the browser, but won't be completed until scanned and found to be clean. Traffic shaping is applied when the file is passed to the browser.
Block potentially unwanted applications: Prevents users from downloading potentially unwanted applications (PUAs).
Authorized PUAs: List of PUAs that you don't want to block.
Action on malware scan failure: Action to take when the firewall encounters content that couldn’t be scanned.
Note
The firewall scans archive files, including up to 16 compression levels. Files that can't be fully scanned because they're encrypted, corrupted, or exceed 16 compression levels may contain undetected threats. Blocking offers the best protection.
Do not scan files larger than: Maximum size of files to be scanned for HTTP(S), in MB. Files that exceed this size won't be scanned.
Note
For compressed files, the firewall considers the compressed size. For example, if the scanning limit for files is 30 MB and a 500 MB file has been compressed to 5 MB, the firewall scans the file.
Maximum file scan size for FTP: Maximum size of files to be scanned for FTP, in MB. Files that exceed this size won't be scanned.
Scan audio and video files: Scans audio and video content for malware and threats. Scanning may cause issues with streaming audio and video.
Enable pharming protection: Pharming attacks redirect users from legitimate websites to fraudulent websites that have been created to look like the legitimate site. Protect users against domain name poisoning attacks by repeating DNS lookups before connecting.
HTTPS decryption and scanning
HTTPS scanning certificate authority (CA): Certificate authority for securing scanned HTTPS connections. This is used only by the web proxy. To configure the CA used by the DPI engine, use Decryption profiles or SSL/TLS inspection settings.
Tip
To download the selected CA certificate, click the download button ![]() next to the drop-down list.
next to the drop-down list.
Block unrecognized SSL protocols: Prevents traffic that avoids HTTPS scanning by using invalid SSL protocols.
Block invalid certificates: Connects only to sites with a valid certificate. The setting applies only to the web proxy. To configure certificate validation settings for the DPI engine, use Decryption profiles.
To turn off certificate validation for specific websites, web categories, or source and destination IP addresses, go to Web > Exceptions.
Block undecrypted connections: The firewall applies policy controls to HTTPS connections even when it isn't configured to decrypt these connections. To make this decision, it uses unencrypted information about the website domain sent by the browser in the initial TLS handshake with the website.
To notify users about a policy action on an HTTPS connection, such as block, warn, quota, or error pages, the firewall must decrypt the connection to send the notification page content to the browser. However, for users' endpoints that don't trust the firewall's signing CA, this may result in the browser showing security warnings.
To control this behavior for sites that aren't usually decrypted, select one of the following notification options:
-
Decrypt connection and show block page: Decrypts the HTTPS connection and shows an HTML notification page that includes the reason for the block.
Note
To prevent browsers from showing a certificate warning, install the scanning CA in users' browsers. See Generate, apply, and install the signing CA.
-
Drop connection without the block page: The firewall drops the connection during the SSL/TLS handshake, and the browser shows a connection failure message. Users don't know why the connection was dropped.
Warning
Some non-browser clients, such as applications communicating with servers or updaters running in the background, may behave differently. Their behavior depends on whether they get a certificate error due to the firewall decrypting the traffic or a connection failure error.
This may cause retry loops in certain situations. Check the web policy to decide whether to block the connection or change the block behavior to allow applications to function properly.
Policy overrides
Policy overrides allow authorized users to grant themselves temporary access to websites that would normally be blocked by a web policy. Authorized users create policy overrides in the user portal, specifying websites and categories, a time range, and access codes. When a user visits a site for which an override is specified, the block page will contain an additional field allowing the user to enter an access code.
- To view and manage the overrides currently specified, select View overrides. These settings allow you to turn overrides on or off and delete overrides.
Enable policy override: Allow authorized users to create web policy overrides in the user portal.
Note
My policy overrides only applies to AD users' main group and to individual users. It doesn't apply to their other group memberships, and the option doesn't appear in the user portal for these memberships.
Authorized users and groups: Users and groups that will be able to create and manage overrides.
Blocked websites and categories: Websites and web categories that can never be bypassed by web policy overrides.
Allow manual access code entry: Allow the specified users to create their own access codes in the user portal. If this option isn't turned on, users must use generated codes.
When the policy override traffic matches an SSL/TLS inspection rule that has action set to Deny, the override won't take effect and the website is blocked. To prevent this, go to Web > Exceptions, and create an exception to skip HTTPS decryption for the matching criteria.
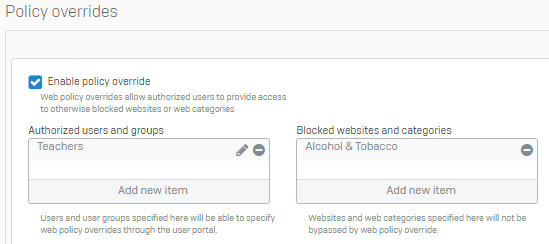
Allow access to blocked websites
The following policy override allows users in the Teachers group to permit end-users access to otherwise blocked websites. However, when the override is in effect, end-users won't be able to access websites in the Alcohol & Tobacco category.
Web content caching
Enable web content cache: Keep a copy of recently visited sites to reduce bandwidth consumption and improve performance.
Sophos Firewall only enforces this with the web proxy.
Web proxy configuration
The firewall intercepts traffic transparently and enforces web protection (for example, policies and malware scanning) when the web proxy service is turned on for a network zone. By default, the service is turned on for LAN and Wi-Fi zones. In transparent mode, the firewall allows HTTP traffic on port 80 and HTTPS traffic on port 443 only.
However, you can configure the firewall to act as a proxy for configured web browsers by specifying a web proxy listening port. Users who are behind the proxy must specify the LAN or Wi-Fi address and port in the web proxy configuration settings of their browsers. (Refer to the browser documentation for details.)
Specify the web proxy listening port and allowed destination ports when you want the firewall to act as a web proxy for configured web browsers.
Note
IPS policy is applicable on the traffic between proxy and WAN, but not between user and proxy.
Note
Traffic shaping policy isn't applicable on the direct proxy traffic.
Web proxy listening port: Port on which the web proxy will listen for HTTP connection requests.
Allowed destination ports: The firewall may receive requests to connect to remote servers using a non-standard port. Specify the ports on which the proxy will allow connection. (This setting applies only when the web proxy listening port is set.)
Warning
Allowing connection on non-standard ports may pose a security risk.
Minimum TLS version: Select the minimum TLS version for both the web proxy and captive portal at the same time.
More resources