Security management and best practices
Here are the best practices when configuring the firewall to protect your network.
Configure zones and scanning rules and policies
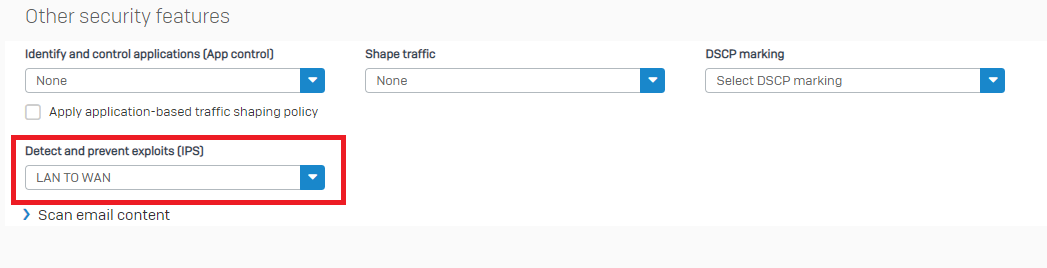
Segregate your networks and apply IPS policies
Separate your networks so any internet-facing services, such as web servers or remote access servers, are on a network segment and zone other than your main LAN network. Place internet-facing services such as these in a DMZ zone and configure firewall rules to block connections from the DMZ to the LAN.
You can also segment other LAN zones as required by using smaller subnets, assigning these to separate LAN zones, and configuring firewall rules to manage traffic between these networks.
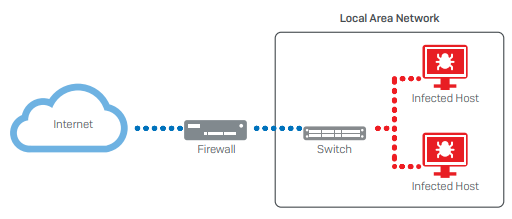
In the following example, the network isn't segmented, allowing the infection to spread easily between endpoints.
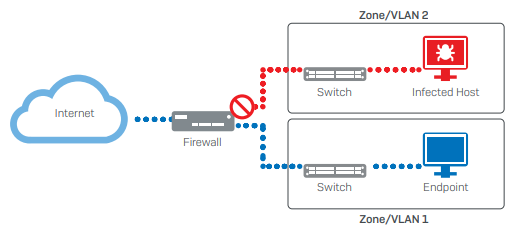
Sophos Firewall prevents infection in one area from spreading to other areas by separating the network into segments, such as the DMZ and LAN networks.
Doing this and applying an IPS policy to rules that govern traffic between these networks reduces the risk of malware or hackers being able to move laterally through your networks if they do manage to perform a successful initial attack. It also provides more time for the threat to be detected and mitigated.
Configure SSL/TLS inspection rules
Configure an SSL/TLS inspection rule to scan most network traffic, with exceptions configured only for services to which SSL scanning will cause problems.
For further details about SSL/TLS inspection rules and how to configure them, see SSL/TLS inspection rules.
Isolate the infected system automatically
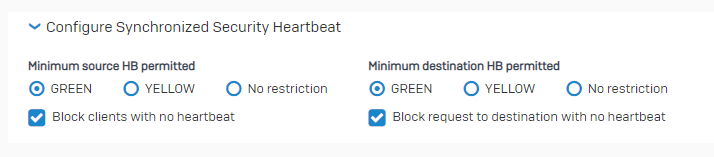
Specify the Synchronized Security Heartbeat settings in firewall rules for the endpoints you manage through Sophos Central.
Security Heartbeat monitors endpoints and automatically isolates those that show signs of infection or compromise from the healthy ones.
For more information, see the following pages:
Access to internal and external resources
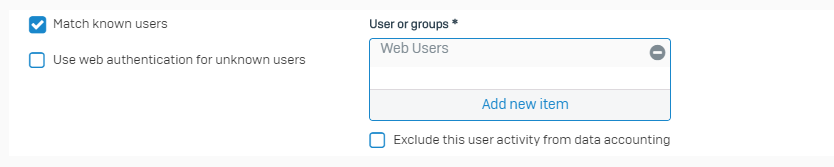
Only allow authenticated LAN users to connect to the internet
When configuring firewall rules to handle user traffic, make sure that you select Match known users. This ensures that only authenticated users can access external resources from within your LAN network.
Secure users' remote access to internal resources
-
Where possible, only allow access to internal resources over a VPN connection, and don't use port forwarding.
- Only allow VPN access to the specified resources for the users and groups that require these resources.
-
Make sure you don't select the default fallback group in remote access VPNs.
Note
The firewall sets Open group as the fallback group by default for adding users to, for example, during Active Directory synchronization if they don't belong to a specific group in the firewall.
Review the group's users periodically and assign them to their correct group.
-
If you must use port forwarding, make sure you apply an IPS policy to the firewall rule that matches the traffic.
Only use NAT for those services that are explicitly needed
Network Address Translation (NAT) allows you to pass traffic easily between different networks. However, only configure NAT rules for services that require it and not for ANY service. Doing this cuts down the surface area malware or hackers can target if one part of your network is breached.
For further information about NAT rules and how to configure them, see NAT rules.
Only allow access to the required countries
Go to Administration > Device access and configure permissions and rules to only allow access to the firewall services for countries necessary for your organization.
-
Global services: These are services, such as Dynamic routing.
- Under Local service ACL, you can allow global permissions from the listed zones.
- Create Local service ACL exception rules to block specific source and destination countries.
-
Specific services: These are services that require high security, such as HTTPS under Admin services, which controls access to the web admin console.
-
Under Local service ACL, don't select access from the WAN zone.
It makes these services vulnerable to threats.
-
Create a Local service ACL exception rule to allow access from specific IP hosts.
-
Implement authentication best practices
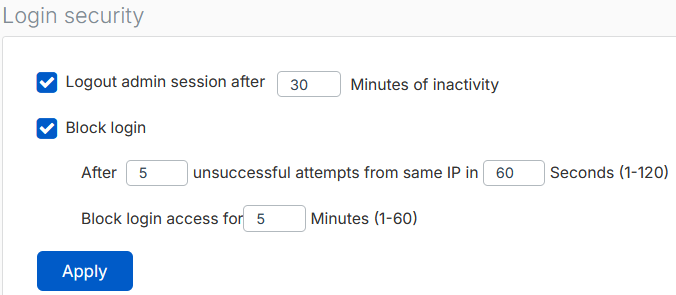
Set up sign-in security and password complexity
Secure the sign-ins as follows:
- Go to Administration > Admin and user settings.
-
Configure the Login security settings.
-
Configure password complexity for administrators and users.
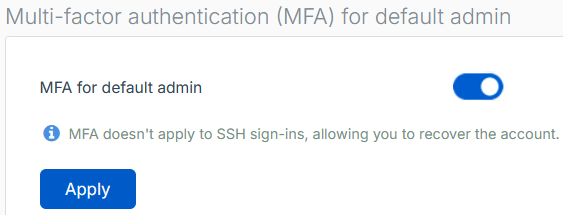
Set up Multi-factor authentication (MFA)
-
Go to Authentication > Device access and configure MFA for the default admin.
-
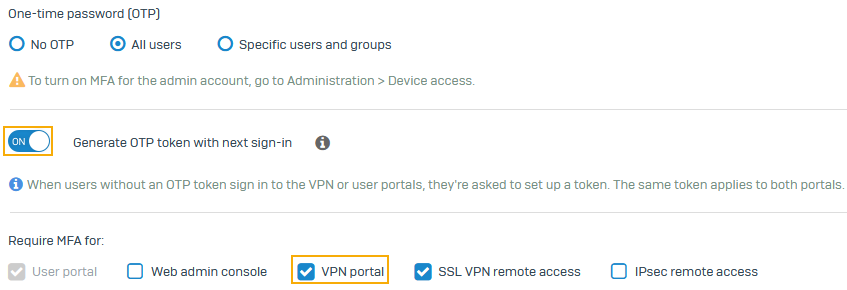
Go to Authentication > Multi-factor authentication (MFA) and configure MFA for all users, if that's possible in your network.
At the least, configure MFA for high-risk groups.
-
Under Require MFA for, make sure you select all the services you use, including the VPN portal and the VPN services that you use.
Note
After you configure MFA, make sure users scan the QR code and generate their OTP tokens as soon as possible. You can see who have generated their tokens under Issued tokens.
For more information, see How to configure Multi-factor authentication and understanding the OTP timestep settings.