Integrate Microsoft Entra Domain Services
Microsoft Entra Domain Services replicates identity information from Microsoft Entra ID (Azure AD) to a set of domain controllers managed by Microsoft. It works with Microsoft Entra ID tenants that are cloud-only or synchronized with an on-premises Active Directory (AD) Domain Services environment. The same features exist for both environments.
You can integrate the firewall with Microsoft Entra ID using Microsoft Entra Domain Services. You can then use the following authentication services:
- Web admin console.
- Captive portal.
- User portal.
- Client authentication agent (CAA) for Windows, macOS, and Linux.
- Remote access SSL VPN.
This guide includes instructions for third-party products. We recommend that you check the vendors' latest documentation.
Requirements
To integrate the firewall with Microsoft Entra ID using Microsoft Entra Domain Services, you must meet the following requirements:
- An existing Microsoft Entra ID configuration. See Configure Microsoft Entra ID (Azure AD) on Azure Portal.
- A Windows, macOS, or Linux endpoint with OpenSSL installed.
Create a self-signed certificate
Microsoft Azure accepts self-signed certificates with extendedKeyUsage set as serverAuth. In this example, we use a Linux machine with OpenSSL to generate a self-signed certificate. Do as follows:
- Run Terminal.
-
Run the following command to create the certificate authority (CA) private key.
Syntax
openssl genrsa -out <name>.key 4096Example
openssl genrsa -out azureADca.key 4096$ openssl genrsa -out azureADca.key 4096 Generating RSA private key, 4096 bit long modulus ..........................................................................................................................................................++ ................++ e is 65537 (0x10001) -
Run the following command to generate the CA certificate. Enter the required values at the prompts. This CA certificate will validate the signed certificates.
Syntax
openssl req -x509 -new -nodes -key <CA private key>.key -days <Number of days> -out <name>.pemExample
openssl req -x509 -new -nodes -key azureADca.key -days 365 -out azureADca.pem$ openssl req -x509 -new -nodes -key azureADca.key -days 365 -out azureADca.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) []:CA State or Province Name (full name) []:ON Locality Name (eg, city) []:Burlington Organization Name (eg, company) []:Sophos Organizational Unit Name (eg, section) []:Sales Engineering Common Name (eg, fully qualified host name) []:sophostest.com Email Address []:admin@sophostest.com -
Copy and paste the following in a text file and save the file as
<name>.conf. For example,azureAD-eku.conf.[client_server_ssl] extendedKeyUsage = serverAuth -
Run the following command to create the LDAP certificate private key.
Syntax
openssl genrsa -out <name>.key 4096Example
openssl genrsa -out ldapssl_private.key 4096$ openssl genrsa -out ldapssl_private.key 4096 Generating RSA private key, 4096 bit long modulus ...................................++ ..........++ e is 65537 (0x10001) -
Run the following command to generate the certificate signing request (CSR). Enter the required values at the prompts.
Syntax
openssl req -new -key <LDAP private key>.key -out <name>.csrExample
openssl req -new -key ldapssl_private.key -out azureADldapssl.csr$ openssl req -new -key ldapssl_private.key -out azureADldapssl.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) []:CA State or Province Name (full name) []:ON Locality Name (eg, city) []:Burlington Organization Name (eg, company) []:firewallinabox Organizational Unit Name (eg, section) []:Sales Engineering Common Name (eg, fully qualified host name) []:firewallinabox.tk Email Address []:admin@firewallinabox.tk Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:testpassword123! -
Run the following command to generate a certificate. The CA signs it based on the CSR.
Syntax
openssl x509 -req -extensions client_server_ssl -extfile <Extended key usage file>.conf -in <Certificate signing request>.csr -CA <CA public key>.pem -CAkey <CA private key>.key -CAcreateserial -out <name>.crt -days <Number of days>Example
openssl x509 -req -extensions client_server_ssl -extfile azureAD-eku.conf -in azureADldapssl.csr -CA azureADca.pem -CAkey azureADca.key -CAcreateserial -out azureADcert.crt -days 365$ openssl x509 -req -extensions client_server_ssl -extfile azureAD-eku.conf -in azureADldapssl.csr -CA azureADca.pem -CAkey azureADca.key -CAcreateserial -out azureADcert.crt -days 365 Signature ok subject=/C=CA/ST=ON/L=Burlington/O=firewallinabox/OU=Sales Engineering/CN=firewallinabox.tk/emailAddress=email@email.com Getting CA Private Key -
Run the following command to convert the certificate to
.pfxformat.Syntax
openssl pkcs12 -export -out <name>.pfx -inkey <LDAP private key>.key -in <Signed certificate>.crt -certfile <CA certificate>.pemExample
openssl pkcs12 -export -out SophosazureADcert.pfx -inkey ldapssl_private.key -in azureADcert.crt -certfile azureADca.pem$ openssl pkcs12 -export -out SophosazureADcert.pfx -inkey ldapssl_private.key -in azureADcert.crt -certfile azureADca.pem Enter Export Password: Verifying - Enter Export Password:
You've created a self-signed certificate. In this example, it's SophosazureADcert.pfx.
Microsoft Azure configuration
Microsoft Entra Domain Services
To integrate the firewall with Microsoft Entra ID using Microsoft Entra Domain Services, do as follows:
- Sign in to Microsoft Azure portal.
-
Configure Microsoft Entra Domain Services. See Tutorial: Create and configure a Microsoft Entra Domain Services managed domain.
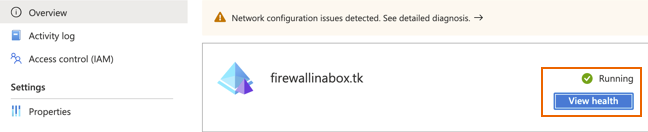
When Microsoft Entra Domain Services is deployed, the status should be Running.
-
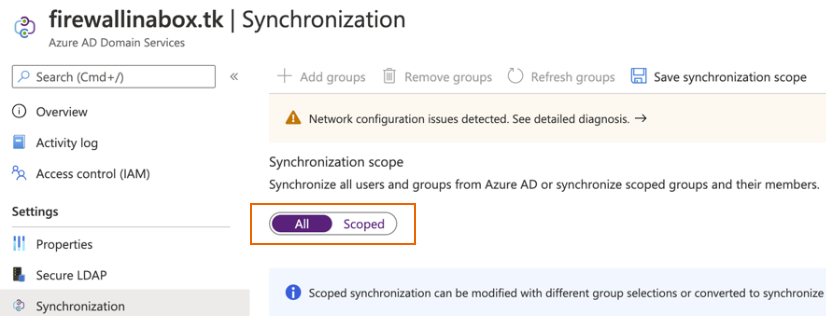
Click Synchronization.
-
Select All or Scoped, then click Save synchronization scope.
Note
Users must sign in to Office 365 and change their password so they can be synchronized with Microsoft Entra Domain Services. Users signing in for the first time are prompted to change their password. This allows the password hashes for Kerberos and NTLM authentication to be generated and stored in Microsoft Entra ID.
-
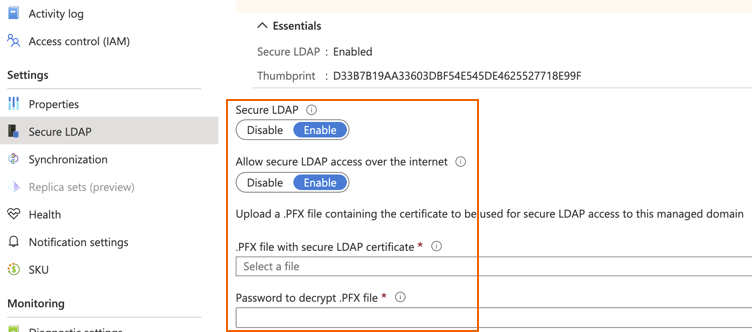
Go to the Microsoft Entra Domain Services you deployed and click Secure LDAP.
- Turn on Secure LDAP and Allow secure LDAP access over the internet.
- Under .PFX file with secure LDAP certificate, upload the
.pfxself-signed certificate you created. -
Under Password to decrypt .PFX file, enter the password to decrypt the file.
-
Click Save.
-
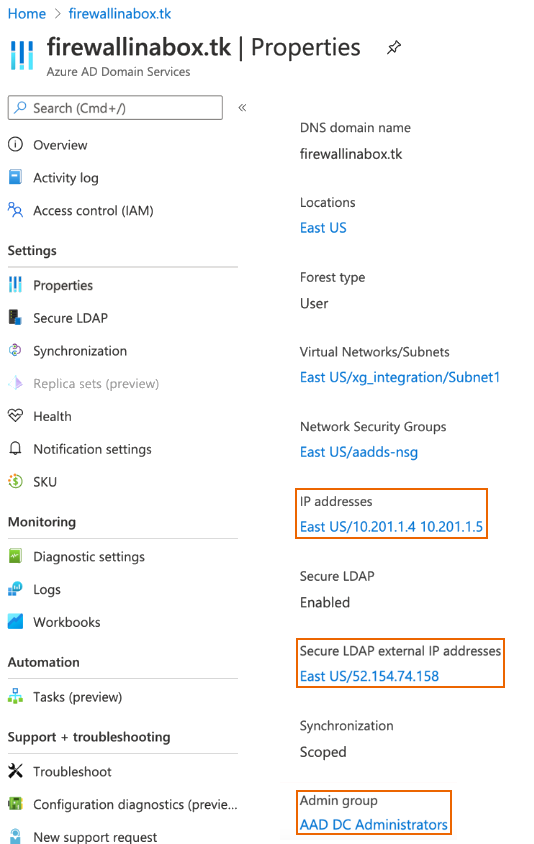
Go to Properties and make a note of the IP addresses, Secure LDAP external IP addresses, and Admin group.
Make sure the configured administrator group is the one used by the firewall to send LDAP bind requests to Microsoft Entra Domain Services.
Check administrator account
To check the administrator account you'll use in the firewall, do as follows:
- Go to Microsoft Entra ID. You can also search for it.
-
Click Users.
Make sure that the administrator account you'll use in the firewall is a member of the configured Admin group in Microsoft Entra Domain Services.
Security rules
To allow LDAPS traffic from the firewall's public IP address, do as follows:
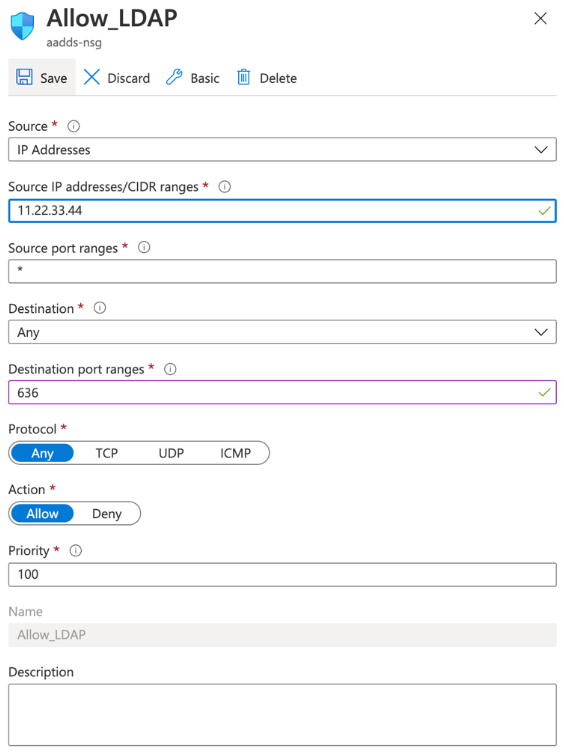
- Go to Network security groups. You can also search for it.
- Click your security group and go to Settings > Inbound security rules.
-
Add an inbound security rule to allow LDAPS traffic from the firewall's public IP address.
-
Sign in to Office 365 using the administrator account you'll use in the firewall. You'll be prompted to change your password.
Firewall configuration
Configure an AD server and import groups
To configure an AD server and import groups, do as follows:
- Sign in to the web admin console.
- Go to Authentication > Servers and click Add.
-
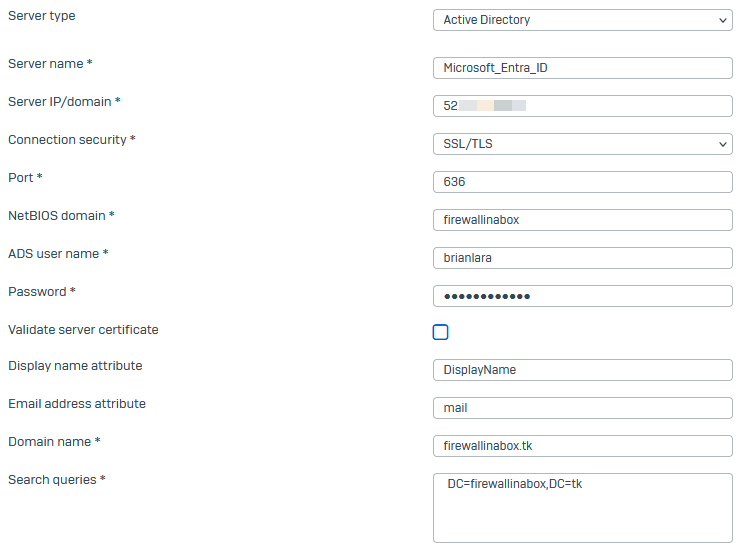
Configure the following settings:
- Server type: Active Directory
- Server name: Enter a name.
- Server IP/domain: Enter your Microsoft Entra ID public IP address.
- Connection security: SSL/TLS
- Port:
636 - NetBIOS domain: Enter the NetBIOS domain.
- ADS user name: Enter the username of the administrator account that's a member of the admin group configured in Microsoft Entra Domain Services.
- Password: Enter the administrator password.
- Validate server certificate: Clear the checkbox.
- Display name attribute:
DisplayName - Email address attribute:
mail - Domain name: Enter your domain.
-
Search queries: Enter your domain's search queries.
-
Test the connection.
- Click Save.
- Import the groups from Microsoft Entra ID. See Import groups.
Authentication services
To use the Microsoft Entra ID server as the authentication method, do as follows:
- Go to Authentication > Services.
- Under Firewall authentication methods, select and apply the Microsoft Entra ID server for the services you want.
You can now authenticate users using Microsoft Entra ID through Microsoft Entra Domain Services.
Tip
For additional security, create an IPsec connection to Microsoft Azure and bind LDAP over it. See Sophos Firewall: Configuring an IPsec VPN Gateway Connection to Azure.