Microsoft Entra ID (Azure AD) server
The firewall supports Microsoft Entra ID single sign-on (SSO) authentication using OAuth 2.0 and OpenID Connect (OIDC) protocols.
Administrators and users can use Microsoft Entra ID SSO to sign in to the following services:
- Web admin console
- Captive portal
- VPN portal
-
Remote access IPsec VPN and remote access SSL VPN through the Sophos Connect client version 2.4 and later in Windows.
Note
For remote access VPN, Microsoft Entra ID SSO uses the VPN portal port to communicate with the firewall. You must allow WAN access for the VPN portal in Administration > Device access, under Local service ACL. See Requirements.
You can import all groups or only those that match specific attributes using the import group assistant. You can also apply schedule and traffic policies. See Import groups.
Microsoft Entra ID SSO supports multi-factor authentication (MFA) configured on your identity provider (IDP). It doesn't support the MFA configured in the firewall.
Set up Microsoft Entra ID SSO
To set up Microsoft Entra ID SSO, you must do as follows:
- Integrate Microsoft Entra ID with Sophos Firewall
- Add a Microsoft Entra ID (Azure AD) server
- Add redirect URIs to Microsoft Entra ID
- Allow Microsoft Azure URLs
Upgrading to SFOS 21.5
If you're using Microsoft Entra ID SSO in SFOS 20.0 or 21.0, upgrading to SFOS 21.5 automatically turns on SSO for services with the authentication method set as Same as firewall.
For example, if your VPN portal, IPsec VPN, or SSL VPN authentication methods are set as Same as firewall, SSO will be turned on for those services. Additionally, to use SSO for the VPN portal, remote access IPsec VPN, or remote access SSL VPN, you must do as follows:
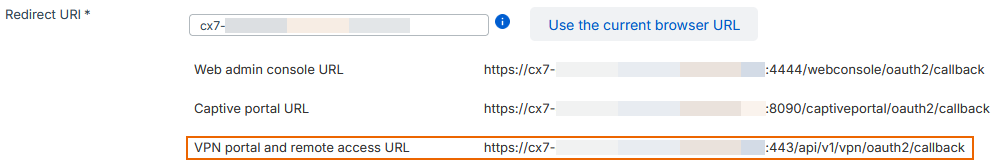
- In the firewall, go to Authentication > Servers.
- Click your Microsoft Entra ID server configuration.
-
Copy the VPN portal and remote access URL.
-
Paste the URL in the application you created for the firewall on Microsoft Entra ID. See Add redirect URIs to Microsoft Entra ID.
Note
If you're configuring Microsoft Entra ID from Sophos Central, don't use the Sophos Central reverse SSO URL.
Videos
Configure Microsoft Entra ID SSO for Sophos Connect
Captive portal authentication

Note
To use Microsoft Entra ID authentication for services, such as web admin console, captive portal, user portal, and client authentication agent (CAA), you can also configure the firewall with Microsoft Entra ID using the Microsoft Entra ID Domain Services. See Sophos Firewall: Integrate Sophos Firewall with Microsoft Entra ID.