Creating Firewall and Masquerading Rules
Defining a Firewall Rule
-
Open the Network Protection > Firewall > Rules page.
-
Click New Rule.
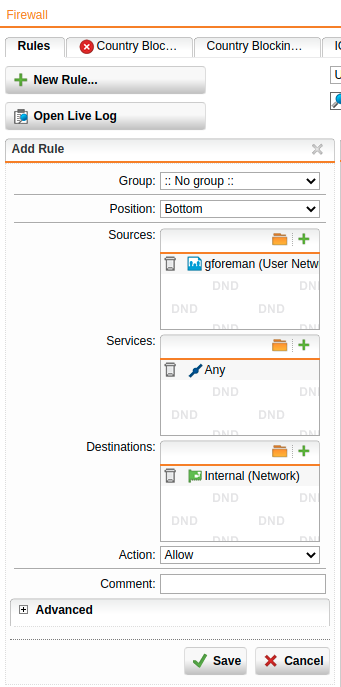
The Add Rule dialog shows.
-
Make the following settings:
Sources: Add the remote user network (in this example: gforeman).
Services: Add the allowed services.
Destinations: Add the allowed networks. Example: Internal (Network). If remote users should be able to access internet you must select the appropriate network definition. Example: Internet or Any.
Action: Select Allow.
-
Click Save.
The firewall rule shows in the list and is turned off (switch is gray).
-
Click the switch to turn on the rule.
The switch turns green.
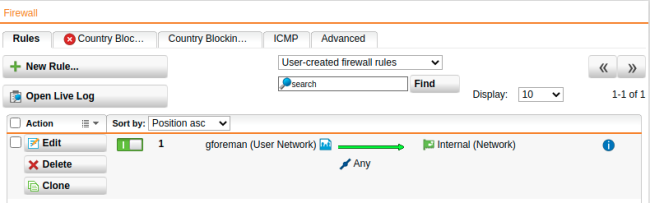
The UTM evaluates active rules from the top down until it finds a match. Once it finds a match, it doesn’t evaluate subsequent rules. So, position the specific rules above the less specific rules.
Security Note: Don’t place a rule such as Any – Any – Any – Allow at the top, since this matches all traffic, and the following rules are never evaluated.
Cross Reference: Find more information about firewall rules in the UTM administration guide under Network Protection.
Create a masquerading rule
Note: This is an optional step depending on your environment.
Masquerading is used to mask the IP addresses of one network with the IP addresses of a second network, in this example: gforeman with External. Thus, remote users who only have private IP addresses can, for example, surf on the internet with a public IP address. Depending on your system configuration, masquerading can also be necessary for other connection types.
-
Go to Network Protection > NAT > Masquerading.
-
Click New Masquerading Rule.
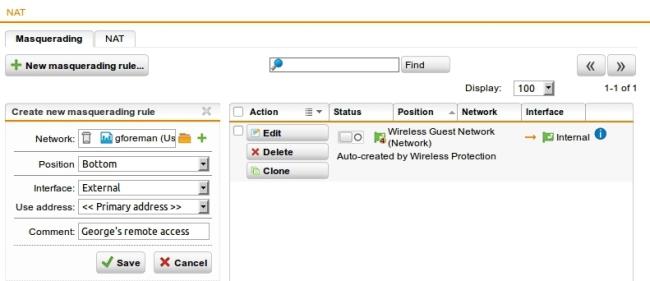
The Add Masquerading Rule dialog shows.
-
Make the following settings:
Network: Select the network of the remote endpoint (in this example: gforeman).
Interface: Select the interface that should be used to mask the clients (in this example: External).
Use address: If the selected interface has more than one IP address, you can define which IP address should be used for masquerading. Default: Primary address.
-
Click Save.
The masquerading rule shows at the end of the list and is turned off (switch shows gray).
-
Click the switch to turn on the rule.
The switch turns green.
Cross Reference: Find more information about masquerading rules in the UTM administration guide under Network Services.
-
Optionally, activate the proxies:
If the remote employees should access URL services via the remote access you may configure the required proxies on the UTM – this would be the DNS and HTTP proxy for example.
Cross Reference: Find more information about proxies in the UTM administration guide.
-
Open the Management > User Portal > Global tab.
You must turn on the User Portal for the remote access users.
If the switch is gray, click the Enable button to turn on the User Portal.
-
Select the networks that are allowed to access the User Portal.
To the Allowed networks box, add the networks that should be allowed to access the User Portal. Example: Any or the respective VPN Pool, or only gforeman).
Cross Reference: Find more information about the User Portal in the UTM administration guide under Management.
Depending on the security policy of your organization and the requirements of your network, you might have to make additional settings.
After configuring the VPN server (headquarter), remote users must configure their devices.