Outbound Gateway for AWS
Sophos UTM on AWS is a solution designed to automatically scale for inbound web application traffic and outbound web content filtering. This solution consists of multiple Sophos UTM units with several roles (Queen & Worker) which work with AWS services. The solution is designed to work across AWS Availability Zones in a single AWS region, and to work with an Internet-facing Elastic Load Balancer that is used to distribute traffic to Sophos UTM Workers for traffic scanning. To use the solution you need to subscribe to Sophos UTM via AWS Marketplace.
OGW (Outbound Gateway) is a setup in AWS where an Auto Scaling group of Sophos UTM units is load-balanced by gateways. The whole setup, Sophos UTM plus gateway, is called Outbound Gateway. OGWs act as outbound load balancers.
The OGW deployment serves two main purposes, firstly scaling of Sophos UTM units to handle increasing outbound traffic loads, and secondly, in some cases, the establishment of a communication path to the Internet for instances that are located within VPCs which lack Internet gateways.
Use cases for the OGW include:
-
VDI access to the Internet (e.g. AWS Workspaces) (main use case)
-
Server instance access to the Internet (including web access)
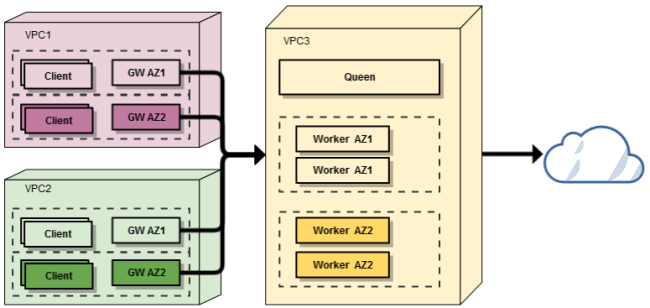
OGW: Concept
The high level architecture of the OGW deployment is shown below. Typical deployment per VPC will consist of three Sophos UTM instances, one controller where configuration is performed, and two workers (one per Availability Zone). Both controller and workers are contained within Auto Scaling groups, which will launch a replacement Sophos UTM should one fail, and workers may also scale under high load. In addition to Sophos UTM units, there are gateway instances which are deployed within each VPC. There is a minimum of two of these per VPC, where they are deployed into separate subnets, and provide High Availability by way of a failover mechanism. To facilitate external traffic routing they connect to Sophos UTM workers via GRE (Generic Routing Encapsulating) tunnels (established during deployment of the gateways).
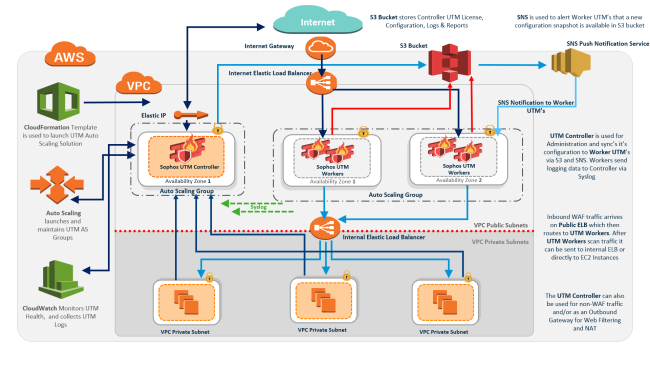
Overview
To use the feature you have to deploy Outbound Gateway(s) for AWS in Sophos UTM. This can be done:
- via the Resource Manager: Sophos UTM will automatically deploy the CloudFormation stack
- manually: Deploying the gateway manually with use of the CloudFormation template
Both methods utilize a CloudFormation template.
Note – You need to decide for a method during object creation. It cannot be changed afterwards.
