Aggressive Mode for IPsec in UTM
Why There's No Aggressive Mode for IPsec in UTM
Aggressive mode is used to authorize the communication partners in phase 1 of establishing an IPsec connection. All Sophos UTM versions, and previous Astaro Security Gateway versions only support main mode. In comparison with aggressive mode, main mode protects the identity of the peers by encrypting the hash values of the preshared key. In aggressive mode, the hash values of the preshared keys are transmitted in plain text. Aggressive mode is required if the IP address of the initiator is unknown and preshared key is selected for authentication.
Workaround for Aggressive Mode
-
Go to Site to Site > IPsec > Remote Gateways.
-
Create a new remote gateway or edit an existing one.
-
Choose Respond only as Gateway type.
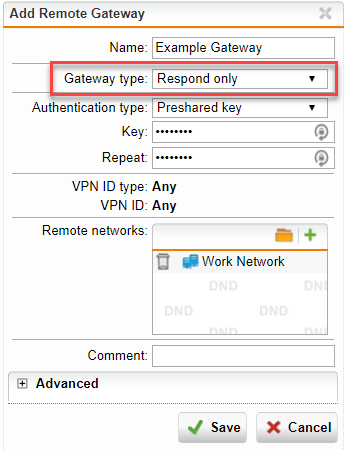
If you are using respond-only mode with PSK authentication you must enable probing of preshared keys.
Another solution is to work with a dynamic DNS provider on the remote side. Inside the IPsec configuration, it's possible to configure the remote gateway with IP or DNS values.
