Sophos Authentication for Thin Client (SATC)
Sophos Authentication for Thin Clients allows users of Windows-based remote desktop services to authenticate with Sophos Firewall using Active Directory.
SATC consists of a component running on your Windows remote desktop server, which sends user information to your Sophos Firewall. The server component is incorporated in Sophos Server Protection.
SATC assigns each user an ID associated with their Active Directory (AD) username. For every outbound network connection created by user activity, such as browsing a website, SATC informs Sophos Firewall which user ID the connection belongs to.
Note
SATC can only authenticate user-based processes. Connections from processes started by system services aren't associated with a directory user. These connections must have a separate firewall rule with Match known users turned off.
To configure SATC with Sophos Server Protection for Windows Remote Desktop Services, download the Windows Server installer from Sophos Central. The installers you see depend on the licenses you have. See Set up SATC with Sophos Server Protection.
SATC has the limitations described in the following sections:
STAS conflicts with SATC
Sophos Transparent Authentication Suite (STAS) provides a solution for clientless SSO. SATC provides SSO on Citrix XenApp and Microsoft Windows Server Remote Desktop Services. Quite often you need to install both STAS and SATC in an organization's network. However, STAS conflicts with SATC, and Sophos Firewall can't obtain the correct user identity on Citrix XenApp and Microsoft Windows Server Remote Desktop Services.
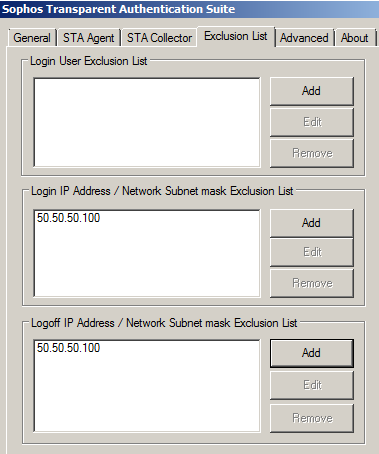
The solution is to exclude the IP addresses of your Citrix XenApp and Microsoft Windows Server Remote Desktop Services in STAS (configured in STAS under Exclusion List > Login IP Address / Network Subnet mask Exclusion List, and Logoff IP Address / Network Subnet mask Exclusion List).
In the example below, 50.50.50.100 is the IP address of the Citrix XenApp server.