How does data control work?
Data control identifies accidental data loss that is typically caused by employees mishandling sensitive data. For example, a user sends a file containing sensitive data home via web-based email.
Data control enables you to monitor and control the transfer of files from computers to storage devices and applications connected to the internet.
- Storage devices:
Data control intercepts all files copied onto monitored storage devices using
Windows Explorer (this includes the Windows desktop). However, direct saves from
within applications, such as Microsoft Word, or transfers made using the command
prompt are not intercepted.
It is possible to force all transfers onto monitored storage devices to be made using Windows Explorer by using either the Allow transfer on acceptance by user and log event action or the Block transfer and log event action. In either case, any attempt to save directly from within an application or transfer files using the command prompt are blocked by data control, and a desktop alert is displayed to the user requesting that they use Windows Explorer to complete the transfer.
When a data control policy only contains rules with the Allow file transfer and log event action, direct saves from within applications and transfers using the command prompt are not intercepted. This behavior enables users to use storage devices without any restrictions. However, data control events are still logged for transfers made using Windows Explorer.
Note This restriction does not apply to application monitoring. - Applications: To ensure only file uploads by users are monitored, some system file locations are excluded from data control monitoring. This significantly reduces the risk of data control events being generated by applications opening configuration files as opposed to users uploading files.
When does data control use on-access scanning exclusions?
Depending on how and where you copy or move files, data control may or may not take into account the on-access scanning exclusions you have set up in the anti-virus and HIPS policy.
Data control uses on-access scanning exclusions when files are uploaded or attached using a monitored application, for example, an email client, a web browser, or an instant messaging (IM) client. For information about configuring on-access scanning exclusions, see Exclude items from on-access scanning.
Data control doesn’t use on-access scanning exclusions when files are copied or moved using Windows Explorer. So the exclusions won’t work, for example, if you copy files to a storage device such as a USB, or copy or move files to a network location. All files will be scanned, even though you may have excluded remote files from on-access scanning.
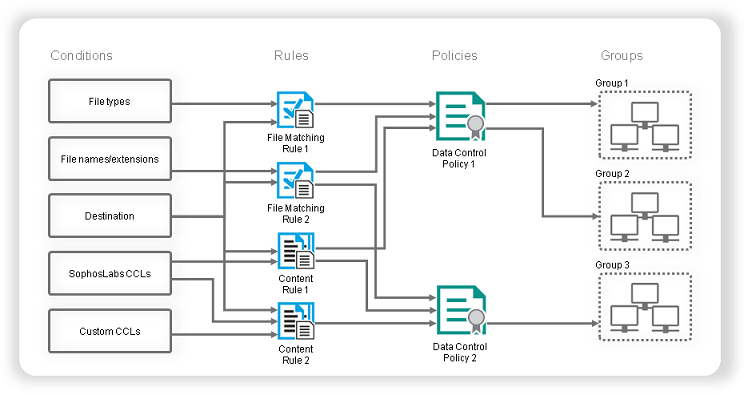
Data control policies
Data control enables you to monitor and control the transfer of files by defining data control policies and applying them to groups of computers on your network.
Data control policies include one or more rules that specify conditions and actions to be taken when the rule is matched. A data control rule can be included in multiple policies.
When a data control policy contains several rules, a file that matches any of the rules in the data control policy violates the policy.
Data control rule conditions
The data control rule conditions include destination, file name and extension, file type, or file content.
Destination includes devices (for example, removable storage devices, such as USB flash drives) and applications (for example, internet browsers and email clients).
The matching of file content is defined using a Content Control List. This is an XML based description of structured data. SophosLabs provide an extensive set of Content Control Lists which can be used within your data control rules.
For more information about data control rules and conditions applied to files, see About data control rules.
For more information about Content Control Lists (CCLs) that define file content, see About Content Control Lists.
Data Control
Data control rule actions
When data control detects all the conditions specified in a rule, the rule is matched, and data control takes the action specified in the rule and logs the event. You can specify one of the following actions:
- Allow file transfer and log event
- Allow transfer on acceptance by user and log event
- Block transfer and log event
If a file matches two data control rules that specify different actions, the rule that specifies the most restrictive action is applied. Data control rules that block file transfer take priority over the rules that allow file transfer on user acceptance. Rules that allow file transfer on user acceptance take priority over the rules that allow file transfer.
By default, when the rule is matched and file transfer is blocked or user confirmation of file transfer is required, a message is displayed on the endpoint computer's desktop. The rule that has been matched is included in the message. You can add your own custom messages to the standard messages for user confirmation of file transfer and for blocked file transfer. For more information, see Set up data control alerts and messages.